Disable Unsafe Protocols with the Ghost Module
One of the things I mentioned in my presentation last fall is the need to disable unsafe protocols that can be leveraged by threat actors. My last few videos have been about how to do that with PowerShell, but after typing these series of random commands, I began to have an idea for a module that could easily assess and disable these commands without having to Google or ChatGPT for them. When thinking of a name, the first thing that came to mind was “Ghost” because I really want my servers to appear to disappear from threat actors should they compromise my network.
The Ghost PowerShell module is designed to enhance the security of Windows servers by providing functionality to disable or assess the status of various protocols and settings. This includes features like PowerShell Remoting, ICMP, NetBIOS, SMBv1, LLMNR, and more. It also checks the execution policy for PowerShell itself.
The module offers two primary cmdlets:
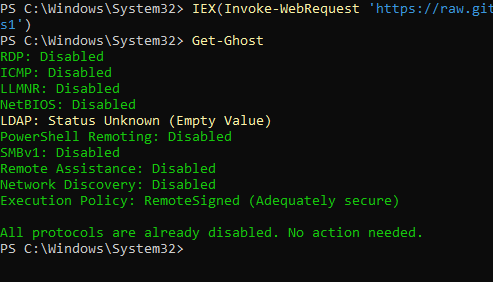
Get-Ghost: Assesses the current configuration of protocols and security settings.
Set-Ghost: Disables insecure protocols and services to harden the system. You can easily run Get-Ghost with this command without even downloading the module:
IEX(Invoke-WebRequest 'https://raw.githubusercontent.com/jimrtyler/Ghost/refs/heads/main/Ghost.ps1') Get-Ghost
Then, run Set-Ghost with the protocol names of protocols you need to disable. For example, Set-Ghost -ICMP -RDP -LLMNR Follow the Ghost repository and myself on Github here: https://github.com/jimrtyler/Ghost